Hosting Ozone behind nginx
Bluesky has released Ozone, a community moderation tool for the network. Although all Bluesky users get the default moderation out of the box, they can also subscribe to any of a number of user-created and run "labelers" (which you can see in this Bluesky list, or on this website).
Some of them label posts with content that could trigger various phobias, some label posts from Twitter, some label AI generated images, some hide spoilers, and some label... posts of beans. Others build an additional entire moderation layer on top of the defaults.
Honestly, I think it's a pretty cool approach to moderation.
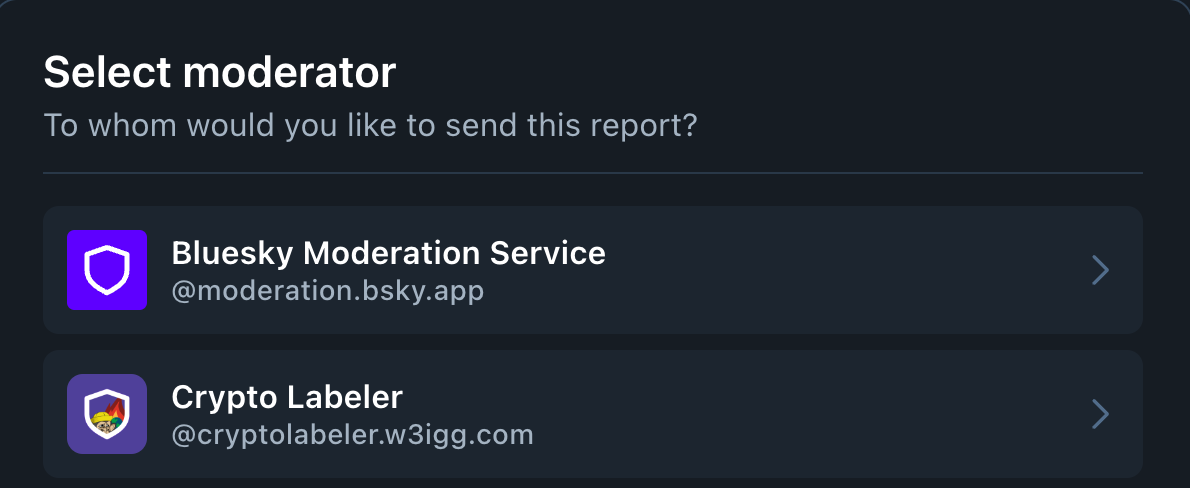
So, of course, I wanted to try it out for myself. I've created a labeler to mark crypto spam: @cryptolabeler.w3igg.com. If you subscribe to the labeler, you'll see some blatant cryptospam posts marked with labels (or hidden, if you choose). You'll also see an option in the reporting screen to report posts to my labeler service:
The setup guide is pretty straightforward, but because it's so new, it doesn't have much detail about running Ozone with different infrastructure. Because I'm running the labeler service on a VPS I use for a few different things, and because I already have nginx running there, I didn't want to stand up Caddy alongside it. So, in case it's helpful to others, here's how I got Ozone running behind nginx:
- Follow the HOSTING.md instructions, but skip the "Create the Caddyfile" step.
- After copying the
compose.yamlfile, delete the entirecaddy:block. - Configure nginx as a reverse proxy. Here's the relevant block in my configuration:
server {
server_name ozone.w3igg.com;
listen 443 ssl; # managed by Certbot
ssl_certificate /etc/letsencrypt/live/ozone.w3igg.com/fullchain.pem; # managed by Certbot
ssl_certificate_key /etc/letsencrypt/live/ozone.w3igg.com/privkey.pem; # managed by Certbot
include /etc/letsencrypt/options-ssl-nginx.conf; # managed by Certbot
ssl_dhparam /etc/letsencrypt/ssl-dhparams.pem; # managed by Certbot
location / {
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header Host $http_host;
# WebSocket support
proxy_http_version 1.1;
proxy_set_header Upgrade $http_upgrade;
proxy_set_header Connection "upgrade";
proxy_pass http://127.0.0.1:3000;
}
}Lines 4–8 are autogenerated by Certbot and shouldn't be added manually. If you want to use Certbot/Let's Encrypt for your SSL certificates, the command is: sudo certbot --nginx -d ozone.w3igg.com (obviously replacing ozone.w3igg.com with your own domain).
I got tripped up while setting this up because I didn't realize Ozone requires a websockets connection. Lines 17–19 should handle that, and Ozone has added some instructions to HOSTING.md to describe how to verify websocket connections are working. Note that if your domain is behind Cloudflare/Fastly/etc. this may require more wrangling.
For more detail on labelers, check out this great blog post by Kairi !