Twitter and its imitators have adopted a structural design that is fundamentally bad for people. This isn't just a matter of who's in charge; it's a problem with the thing itself. Forcing users to adhere to a tight character limit, discouraging link culture, preventing people from editing their own posts, steering people into sharing things they hate, incentivizing rage bait with trending feeds, subjecting people to decontextualized encounters, encouraging conflict by discouraging tags, and leaving users powerless to clean up the resulting mess—all of this is bad shape.
Activity tagged "social media"
Exciting: The Ghost team has just released the beta version of its ActivityPub support for people using their hosted service
social media platform users are going to link offsite. the only question is how obnoxious the platform will make it for them and everyone else.
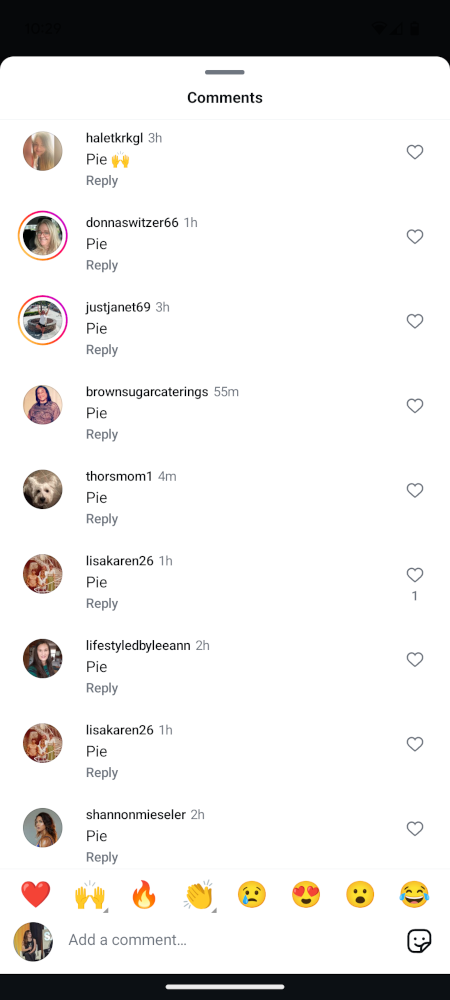
(For context: Instagram prohibits links in post text. This, plus the incentive to inflate comments, has led to the proliferation of tools where creators instruct their followers to comment with a specific word to receive a link in their DMs — in this case, to a pie crust recipe)
Great piece on BlueSky and enshittification by Cory Doctorow . “I will never again devote my energies to building up an audience on a platform whose management can sever my relationship to that audience at will.” I also really appreciate his point that it’s not the blockchain venture capital that leads to enshittification, it’s the venture capital.
Cory is a fellow POSSE-er (and major inspiration to me when I adopted the practice), and has opted not to use Bluesky. Personally, I’ve gone the route of using the platforms that interest me, even the enshittification-prone ones like Bluesky and Threads, but hedging my bets by plugging them into my POSSE system where they can just as easily be unplugged if need be.
Some weeks ago, I quietly shipped a new content type on A Working Library, such that I am now writing short, social-shaped posts on my site and then sending them off to the various platforms. This is not a novel mode of publishing, but rather one borrowed and adapted from the POSSE model (“publish on your site, syndicate elsewhere”) developed by the IndieWeb community. While one of the reasons oft declared for using POSSE is the ability to own your content, I’m less interested in ownership than I am in context. Writing on my own site has very different affordances: I’m not typing into a little box, but writing in a text file. I’m not surrounded by other people’s thinking, but located within my own body of work. As I played with setting this up, I could immediately feel how that would change the kinds of things I would say, and it felt good. Really good. Like putting on a favorite t-shirt, or coming home to my solid, quiet house after a long time away.
POSSE: Reclaiming social media in a fragmented world
oh no (h/t Robert Stephens)
I had such a great chat with Mike McCue on his Dot Social podcast, where we talked about the future of the web and why I'm a web optimist, why everyone should be a blogger, digital ownership, and decentralized social media.
The full episode is available here and on PeerTube/YouTube/the usual podcast feeds!
Infra stack: from AWS to on-prem. AWS was becoming too costly, so Bluesky moved over to dedicated data centers and bare-metal machines.
That's not something you read every day.
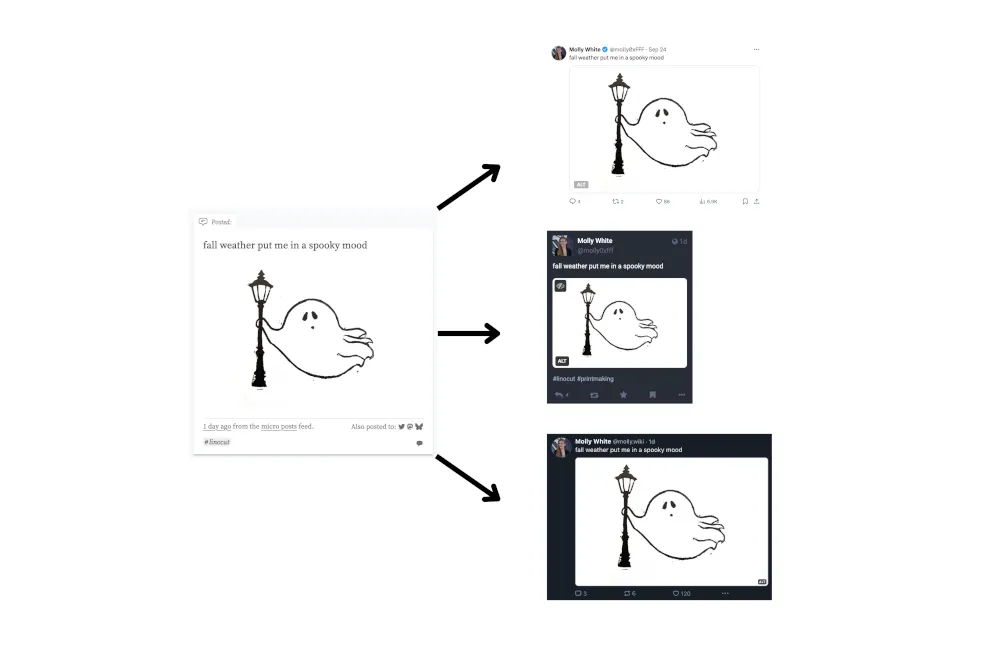
![Threads search bar with “molly white” typed in. Warning message: “This may be associated with the sale of drugs
The sale, purchase, or trade of illicit drugs can cause harm to yourself and others and is illegal in most countries. If you or someone you know struggle with substance abuse, you can get help through confidential treatment referrals, prevention, and recovery support.
[Button:] Get help ”](https://storage.mollywhite.net/micro/1c4cda9af79b66115e1e_6bb33b28fe57b6a1.png)